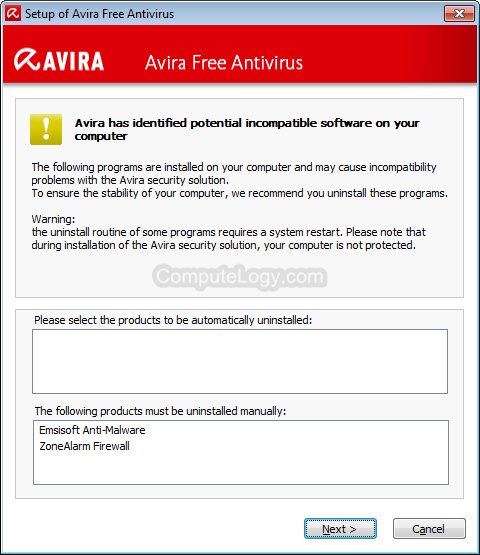
Manually Update Comodo Virus Definitions
Posted : adminOn 12/2/2017Others SignaturesUpdates Downloadssort by Definition bases for Zillya Antivirus and Zillya Internet Security, allowing you to update the v. Dec 3rd 2. 01. 7, 2. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista Windows XPSignature packages containing the latest free virus databases for various Symantec antivirus softw. Dec 3rd 2. 01. 7, 2. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XPThe latest unstable update for The Bat, an alternative e mail client for advanced e mail users fo. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XPKeep Vipre up to date with the latest definition files by manually installing the required package. Comodo%20Antivirus%20for%20MAC/bf193985d9cc0f23d51a6081f03ca78e/5eac818f1e1c4adc19d335055b06586b/5ef7f86e10711f3aef7bab66efa5e05c/howto_update1.png' alt='Manually Update Comodo Virus Definitions' title='Manually Update Comodo Virus Definitions' /> Dec 3rd 2. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Best free antivirus 2017 The six top choices for protecting your PC from malware and viruses including Kaspersky, AVG and Avast. Manually Update Comodo Virus Definitions' title='Manually Update Comodo Virus Definitions' />Norton AntiVirus is an antimalware software developed and distributed by Symantec Corporation since 1991 as part of its Norton family of computer security products. R5j_GieKg8/TjAb70DIS7I/AAAAAAAACW8/Xm5xwBWJl60/s1600/kaspersky+2012+updating+disk+image+wizard.jpg' alt='Manually Update Comodo Virus Definitions' title='Manually Update Comodo Virus Definitions' />Windows Vista Windows XP 6. Windows XPKeep SUPERAnti. Spyware up to date with the latest definitions even if your computer is not connecte. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 Windows 8 Windows 7 Windows Vista Windows XPInstall the latest Windows Defender definition updates and make sure your computer is safe from vi. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista. Manually install the latest antivirus definitions for Microsoft Security Essentials in case your c. Dec 3rd 2. 01. 7, 1. GMTWindows 7 6. 4 bit Windows 7 Windows Vista 6. Windows Vista. A specialized definitions database that you can rely on to keep your edition of IObit Malware Figh. Cricket 07 Tournament Editor. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 2. Windows 2. 00. 3 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista Windows XPThe latest virus definitions for your Avast antivirus, providing an alternative method to keep the. Dec 3rd 2. 01. 7, 1. GMTWindows All. Download the virus definitions file to easily always keep versions 1. Avi. Dec 3rd 2. 01. GMTWindows All. Contains the latest virus definitions for the F Secure product line, including Workstation, Antivi. Dec 3rd 2. 01. 7, 1. GMTWindows All. Update your Comodo Antivirus or Internet Security database to its latest version by using this pac. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XPUpdate Windows 1. Version 1. 60. 7 Anniversary Update to KB4. Version 1. 70. 3 Creators Update t. Dec 3rd 2. 01. 7, 1. GMTWindows Server 2. Windows 1. 0 6. 4 bit Windows 1. Driver updater with support for backup, restore, uninstall and reinstall, wrapped in an intuitive interface with approachable options. Filter your traffic, scan for vulnerabilities, patch and update important third party software using this straightforward and reliable software solution that helps improve the security of your home PC or corporate network. A powerful All In One PC Care Service software solution with anti spyware, privacy protection and a lot of performance tune ups available. Easily hide important or personal files, folders or even an entire USB Drive with only a few mouse clicks, keeping them safe with a password. Scan your files in order to detect any malware or other security threats, then easily remove them, by using this fast and powerful application. Update all your drivers and game components, activate a silent update mode popup notifications are disabled and automatically create a restore point. File download accelerator with browser integration, task scheduler, automatic post task actions, malware checker, MD5 and SHA1 verifier, Clipboard and browser monitoring, media grabber, video sniffer, and task cleaner. Keep all your installed software applications up to date using this simple app that automatically scans the computer and reveals available updates. Create and customize titles or subtitles for your various projects by embedding them directly into the video file using this application. Edit videos using three different modes, special effects, transitions and create discs using the built in burning options that this application provides. Resort to this all encompassing video player to watch clips in any popular file format and enjoy the benefits of 3. VR support, and many other advanced features. A feature packed software solution that helps you create backups for files, folders and partitions, then restore data when needed. SUMo. SUMotitlebee subtitle editor. Cyber. Link Power. Director. GOM Player Plus. AOMEI Backupper Professional. Driver Talent. Heimdal PROAdvanced System. Care Pro. Wise Folder Hider. El Libro Magno De La Cruz De Caravaca Pdf'>El Libro Magno De La Cruz De Caravaca Pdf. Zemana Anti. Malware Premium. Driver Booster. Eagle. Getessentials. The latest free virus definitions for AVG Antivirus, which you can use to perform manual updates i. Dec 3rd 2. 01. 7, 0. GMTWindows All. Manually update Ikarus Virus Utilities and T3 Command Line Scanner by using this file that provide. Dec 3rd 2. 01. 7, 0. GMTWindows All. A collection of Virus Pattern Files that are updated to their latest virus database definitions an. Dec 3rd 2. 01. 7, 0. GMTUnix Windows All. Download Mc. Afee virus pattern and engine updates and make sure that your Mc. Afee antivirus can prot. Dec 3rd 2. 01. 7, 0. GMTWindows All. Update the virus definitions database of your K7 Security Product on a computer which isnt connec. Dec 3rd 2. 01. 7, 0. GMTWindows All. The files you need to keep Malwarebytes Anti Malware up to date in case your computer is no longer. Dec 2nd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XPDaily signature and virus definitions updates for your Quick Heal products, allowing the manual up. Dec 2nd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows Server 2. Windows 2. 00. 8 R2 Windows 2. Windows 2. 00. 8 Windows 2. Windows 8 6. 4 bit Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XP Windows 2. KThe up to date virus signature files for the Clam. AV antivirus, which can be downloaded in case the. Dec 1st 2. 01. 7, 2. GMTWindows All. Manually update the definitions of the following Bitdefender products Total Security 2. Intern. Dec 1st 2. GMTWindows All. The latest virus definitions for Bit. Defender Antivirus, Bit. Defender Antivirus Plus and Bit. Defender. Dec 1st 2. GMTWindows All. Keep REVE Antivirus, Internet Security and Total Security up to date with the latest virus definit. Dec 1st 2. 01. 7, 0. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista. Keep your Clam. Win Free Antivirus definition database up to date by manually adding database files. Nov 3. 0th 2. 01. GMTWindows All. Update the definitions of your Spybot Search and Destroy manually without requiring the Web. Updat. Nov 2. 9th 2. GMTWindows All. View out of date applications on your computer, download the latest available versions and install. Nov 2. 7th 2. 01. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XPMake sure that the applications installed on your computer are updated to their latest version and. Nov 2. 0th 2. 01. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Using a Free Online Malware Analysis Sandbox to Dig Into Malicious Code. The continuous advancement and sophistication of cyberthreats has gradually decreased the sufficiency of traditional gateway and endpoint security solutions for protection against malware. These approaches were sufficient when malware occurred in small numbers and it was easy to differentiate between good and bad applications. Nowadays, theres a world of unknown code a gap between known good and known bad code that can pose a serious risk to your environment. How do you determine whether unknown code is good or bad You let it run in a malware analysis sandbox a safe environment that closely resembles your real infrastructure and observe its behavior. This allows you to learn how the malware would affect your systems and extract information about the detailed behavior of the code. In the case of malicious code, this information is called indicators of compromise Io. Cs. These indicators can later be used to update your existing security solutions or detect infections that already took place. Read the white paper Evading the Malware Sandbox Comparing Four Traditional Public Malware Analysis Sandboxes. In 2. 01. 5, we compared four free online malware analysis sandbox solutions Virus. Total, Anubis, Vx. Stream and Malwr. Over the last two years, these solutions have evolved along with the threat landscape. Anubis is no longer available as a free product. That leaves three public solutions, each with its own approach Virus. Total rates detection by different antivirus engines. Vx. Stream reports on malware behavior, including screen shots and YARA rule matching. Malwr is Cuckoo with the capability to report on malware behavior, including screen shots. Lets take a closer look at these three solutions. Virus. Total. Virus. Total is a popular solution in the security community for file analysis and remains available as a free service. Virus. Total reports include the detection results of the malware by different antivirus engines and community generated feedback to enrich the analysis details. This solution allows you to analyze both individual files and websites. Over the last two years, the number of scanners included with Virus. Total has increased to support scanning of firmware malware. The solution is now also capable of handling Mac OS X apps in addition to Windows and Android. Virus. Total offers both free and paid access. The paid solution allows you to Submit requests at a higher rate. Extract more behavioral execution information. Retrieve additional metadata information from submission. Receive YARA notifications on the samples collected by Virus. Total. Vx. Stream. Vx. Stream by Payload Security takes a slightly different approach than Virus. Total. Vx. Stream displays the results of the malware analysis in detail, including screen shots and extracted strings from the submitted file. Compared to Virus. Total, the analysis of Vx. Stream is more in depth and closer to what you would expect from a malware analysis tool you would run in your own lab. The solution also provides URL based analysis, but only if the URL contains a file. Vx. Stream now also includes support for Windows XP, Vista, Windows 78 and 1. Android APK files Additional import formats, including MIME RFC 8. Outlook. msg files Additional export formats, including MAEC 4. Open. IOC 1. 1 and STIX MISP reports, both in XML and JSON and. Integration with Virus. Total and OPSWAT Metadefender. The free version of Vx. Stream allows you to download the samples and packet capture PCAP files. Reports include screen shots of the malware behavior. Note that the free version will not display all malicious and suspicious indicators. Similar to Virus. Total, Vx. Stream also has a paid version with support for URL analysis Information on all malicious and suspicious indicators found Submitting requests at a higher rate Full privacy for your reports and. ARA. Malwr. Malwr is based on a Cuckoo malware sandbox analysis. In fact, the site is maintained by the core developers of Cuckoo. The benefit of the service is that you do not have to bother setting up Cuckoo yourself and can let Malwr do the heavy lifting. The solutions uses the new Cuckoo Sandbox 2. Malwr only allows you to analyze files it is not possible to submit URLs. Reports from Malwr include screen shots, offering visual information on the malware behavior. Some reports also include community comments. Analyses from Malwr can be visualized at Malware. Viz. Popular Alternatives. Besides the three malware sandbox solutions listed previously, what other options are available Lets review some of the most popular alternatives. Antivirus Vendors. An oft forgotten option is to send the malware sample to your antivirus vendor. Unfortunately, not all vendors provide detailed technical reports on the behavior of the malware. The analysis is essentially limited to checking whether an antivirus engine detects a specific sample. Virus. Total also provides this capability. Some upload centers include Mc. Afee for submitting viruses or malware samples F Secure for submitting samples Bitdefender for submitting samples or URLs Trend Micro for submitting suspicious or undetected viruses for file analysis and. Kaspersky Virus Desk. Linux Malware. Most public malware sandboxes focus on Windows binaries and, in some cases, Android files. Detux, by the Indian Honeynet Project, is a Linux sandbox with support for x. ARM, MIPS and MIPSEL central processing unit CPU architectures. Valkyrie. Valkyrie is a file verdict system by Comodo that analyzes the entire runtime behavior of a file. The web interface is intuitive and rich with features. Unfortunately, the detection rate of submitted samples was fairly low the solution rated the samples as No Threat found. Valkyrie includes a free service and a paid service with more support options. Commercial Malware Sandboxes. A fourth alternative is using a malware sandbox that is not available for free, although commercially available malware solutions are sometimes heavily priced. An alternative is VMRay, a malware analyzer that you can use during incident response. VMRay is invisible to malware. Sat File Viewer Free Download. It is embedded in the hypervisor and analyzes malware behavior from that vantage point. As a result, threats execute as they would in the wild. This analysis provides a full function log, which allows you to understand the execution steps of the malware. You can use a web interface to log into the sandbox environment where the malware is executing, possibly simulating the behavior of a normal user. VMRay is not available for free, but nearly everyone can get a 3. Some of these accounts can be extended by exception for researchers without budget, for example for free on an annual basis. Be Careful What You Share. Anything that you share with a public resource is accessible to everyone including the bad guys. Always verify that the sample youre about to upload does not contain confidential or sensitive information. Instead of submitting the file, you can also generate the file hash and verify whether the hash is known by the sandbox. This allows you to access the analysis details, provided the file has been analyzed before, without submitting your actual sample. You may also want to investigate whether the sample is targeted specifically to you. Uploading it to a public sandbox makes the attacker aware of the malware detection.
Dec 3rd 2. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Best free antivirus 2017 The six top choices for protecting your PC from malware and viruses including Kaspersky, AVG and Avast. Manually Update Comodo Virus Definitions' title='Manually Update Comodo Virus Definitions' />Norton AntiVirus is an antimalware software developed and distributed by Symantec Corporation since 1991 as part of its Norton family of computer security products. R5j_GieKg8/TjAb70DIS7I/AAAAAAAACW8/Xm5xwBWJl60/s1600/kaspersky+2012+updating+disk+image+wizard.jpg' alt='Manually Update Comodo Virus Definitions' title='Manually Update Comodo Virus Definitions' />Windows Vista Windows XP 6. Windows XPKeep SUPERAnti. Spyware up to date with the latest definitions even if your computer is not connecte. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 Windows 8 Windows 7 Windows Vista Windows XPInstall the latest Windows Defender definition updates and make sure your computer is safe from vi. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista. Manually install the latest antivirus definitions for Microsoft Security Essentials in case your c. Dec 3rd 2. 01. 7, 1. GMTWindows 7 6. 4 bit Windows 7 Windows Vista 6. Windows Vista. A specialized definitions database that you can rely on to keep your edition of IObit Malware Figh. Cricket 07 Tournament Editor. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 2. Windows 2. 00. 3 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista Windows XPThe latest virus definitions for your Avast antivirus, providing an alternative method to keep the. Dec 3rd 2. 01. 7, 1. GMTWindows All. Download the virus definitions file to easily always keep versions 1. Avi. Dec 3rd 2. 01. GMTWindows All. Contains the latest virus definitions for the F Secure product line, including Workstation, Antivi. Dec 3rd 2. 01. 7, 1. GMTWindows All. Update your Comodo Antivirus or Internet Security database to its latest version by using this pac. Dec 3rd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XPUpdate Windows 1. Version 1. 60. 7 Anniversary Update to KB4. Version 1. 70. 3 Creators Update t. Dec 3rd 2. 01. 7, 1. GMTWindows Server 2. Windows 1. 0 6. 4 bit Windows 1. Driver updater with support for backup, restore, uninstall and reinstall, wrapped in an intuitive interface with approachable options. Filter your traffic, scan for vulnerabilities, patch and update important third party software using this straightforward and reliable software solution that helps improve the security of your home PC or corporate network. A powerful All In One PC Care Service software solution with anti spyware, privacy protection and a lot of performance tune ups available. Easily hide important or personal files, folders or even an entire USB Drive with only a few mouse clicks, keeping them safe with a password. Scan your files in order to detect any malware or other security threats, then easily remove them, by using this fast and powerful application. Update all your drivers and game components, activate a silent update mode popup notifications are disabled and automatically create a restore point. File download accelerator with browser integration, task scheduler, automatic post task actions, malware checker, MD5 and SHA1 verifier, Clipboard and browser monitoring, media grabber, video sniffer, and task cleaner. Keep all your installed software applications up to date using this simple app that automatically scans the computer and reveals available updates. Create and customize titles or subtitles for your various projects by embedding them directly into the video file using this application. Edit videos using three different modes, special effects, transitions and create discs using the built in burning options that this application provides. Resort to this all encompassing video player to watch clips in any popular file format and enjoy the benefits of 3. VR support, and many other advanced features. A feature packed software solution that helps you create backups for files, folders and partitions, then restore data when needed. SUMo. SUMotitlebee subtitle editor. Cyber. Link Power. Director. GOM Player Plus. AOMEI Backupper Professional. Driver Talent. Heimdal PROAdvanced System. Care Pro. Wise Folder Hider. El Libro Magno De La Cruz De Caravaca Pdf'>El Libro Magno De La Cruz De Caravaca Pdf. Zemana Anti. Malware Premium. Driver Booster. Eagle. Getessentials. The latest free virus definitions for AVG Antivirus, which you can use to perform manual updates i. Dec 3rd 2. 01. 7, 0. GMTWindows All. Manually update Ikarus Virus Utilities and T3 Command Line Scanner by using this file that provide. Dec 3rd 2. 01. 7, 0. GMTWindows All. A collection of Virus Pattern Files that are updated to their latest virus database definitions an. Dec 3rd 2. 01. 7, 0. GMTUnix Windows All. Download Mc. Afee virus pattern and engine updates and make sure that your Mc. Afee antivirus can prot. Dec 3rd 2. 01. 7, 0. GMTWindows All. Update the virus definitions database of your K7 Security Product on a computer which isnt connec. Dec 3rd 2. 01. 7, 0. GMTWindows All. The files you need to keep Malwarebytes Anti Malware up to date in case your computer is no longer. Dec 2nd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XPDaily signature and virus definitions updates for your Quick Heal products, allowing the manual up. Dec 2nd 2. 01. 7, 1. GMTWindows 1. 0 6. Windows 1. 0 Windows Server 2. Windows 2. 00. 8 R2 Windows 2. Windows 2. 00. 8 Windows 2. Windows 8 6. 4 bit Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XP Windows 2. KThe up to date virus signature files for the Clam. AV antivirus, which can be downloaded in case the. Dec 1st 2. 01. 7, 2. GMTWindows All. Manually update the definitions of the following Bitdefender products Total Security 2. Intern. Dec 1st 2. GMTWindows All. The latest virus definitions for Bit. Defender Antivirus, Bit. Defender Antivirus Plus and Bit. Defender. Dec 1st 2. GMTWindows All. Keep REVE Antivirus, Internet Security and Total Security up to date with the latest virus definit. Dec 1st 2. 01. 7, 0. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista. Keep your Clam. Win Free Antivirus definition database up to date by manually adding database files. Nov 3. 0th 2. 01. GMTWindows All. Update the definitions of your Spybot Search and Destroy manually without requiring the Web. Updat. Nov 2. 9th 2. GMTWindows All. View out of date applications on your computer, download the latest available versions and install. Nov 2. 7th 2. 01. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Windows Vista Windows XP 6. Windows XPMake sure that the applications installed on your computer are updated to their latest version and. Nov 2. 0th 2. 01. GMTWindows 1. 0 6. Windows 1. 0 Windows 8 6. Windows 8 Windows 7 6. Windows 7 Windows Vista 6. Using a Free Online Malware Analysis Sandbox to Dig Into Malicious Code. The continuous advancement and sophistication of cyberthreats has gradually decreased the sufficiency of traditional gateway and endpoint security solutions for protection against malware. These approaches were sufficient when malware occurred in small numbers and it was easy to differentiate between good and bad applications. Nowadays, theres a world of unknown code a gap between known good and known bad code that can pose a serious risk to your environment. How do you determine whether unknown code is good or bad You let it run in a malware analysis sandbox a safe environment that closely resembles your real infrastructure and observe its behavior. This allows you to learn how the malware would affect your systems and extract information about the detailed behavior of the code. In the case of malicious code, this information is called indicators of compromise Io. Cs. These indicators can later be used to update your existing security solutions or detect infections that already took place. Read the white paper Evading the Malware Sandbox Comparing Four Traditional Public Malware Analysis Sandboxes. In 2. 01. 5, we compared four free online malware analysis sandbox solutions Virus. Total, Anubis, Vx. Stream and Malwr. Over the last two years, these solutions have evolved along with the threat landscape. Anubis is no longer available as a free product. That leaves three public solutions, each with its own approach Virus. Total rates detection by different antivirus engines. Vx. Stream reports on malware behavior, including screen shots and YARA rule matching. Malwr is Cuckoo with the capability to report on malware behavior, including screen shots. Lets take a closer look at these three solutions. Virus. Total. Virus. Total is a popular solution in the security community for file analysis and remains available as a free service. Virus. Total reports include the detection results of the malware by different antivirus engines and community generated feedback to enrich the analysis details. This solution allows you to analyze both individual files and websites. Over the last two years, the number of scanners included with Virus. Total has increased to support scanning of firmware malware. The solution is now also capable of handling Mac OS X apps in addition to Windows and Android. Virus. Total offers both free and paid access. The paid solution allows you to Submit requests at a higher rate. Extract more behavioral execution information. Retrieve additional metadata information from submission. Receive YARA notifications on the samples collected by Virus. Total. Vx. Stream. Vx. Stream by Payload Security takes a slightly different approach than Virus. Total. Vx. Stream displays the results of the malware analysis in detail, including screen shots and extracted strings from the submitted file. Compared to Virus. Total, the analysis of Vx. Stream is more in depth and closer to what you would expect from a malware analysis tool you would run in your own lab. The solution also provides URL based analysis, but only if the URL contains a file. Vx. Stream now also includes support for Windows XP, Vista, Windows 78 and 1. Android APK files Additional import formats, including MIME RFC 8. Outlook. msg files Additional export formats, including MAEC 4. Open. IOC 1. 1 and STIX MISP reports, both in XML and JSON and. Integration with Virus. Total and OPSWAT Metadefender. The free version of Vx. Stream allows you to download the samples and packet capture PCAP files. Reports include screen shots of the malware behavior. Note that the free version will not display all malicious and suspicious indicators. Similar to Virus. Total, Vx. Stream also has a paid version with support for URL analysis Information on all malicious and suspicious indicators found Submitting requests at a higher rate Full privacy for your reports and. ARA. Malwr. Malwr is based on a Cuckoo malware sandbox analysis. In fact, the site is maintained by the core developers of Cuckoo. The benefit of the service is that you do not have to bother setting up Cuckoo yourself and can let Malwr do the heavy lifting. The solutions uses the new Cuckoo Sandbox 2. Malwr only allows you to analyze files it is not possible to submit URLs. Reports from Malwr include screen shots, offering visual information on the malware behavior. Some reports also include community comments. Analyses from Malwr can be visualized at Malware. Viz. Popular Alternatives. Besides the three malware sandbox solutions listed previously, what other options are available Lets review some of the most popular alternatives. Antivirus Vendors. An oft forgotten option is to send the malware sample to your antivirus vendor. Unfortunately, not all vendors provide detailed technical reports on the behavior of the malware. The analysis is essentially limited to checking whether an antivirus engine detects a specific sample. Virus. Total also provides this capability. Some upload centers include Mc. Afee for submitting viruses or malware samples F Secure for submitting samples Bitdefender for submitting samples or URLs Trend Micro for submitting suspicious or undetected viruses for file analysis and. Kaspersky Virus Desk. Linux Malware. Most public malware sandboxes focus on Windows binaries and, in some cases, Android files. Detux, by the Indian Honeynet Project, is a Linux sandbox with support for x. ARM, MIPS and MIPSEL central processing unit CPU architectures. Valkyrie. Valkyrie is a file verdict system by Comodo that analyzes the entire runtime behavior of a file. The web interface is intuitive and rich with features. Unfortunately, the detection rate of submitted samples was fairly low the solution rated the samples as No Threat found. Valkyrie includes a free service and a paid service with more support options. Commercial Malware Sandboxes. A fourth alternative is using a malware sandbox that is not available for free, although commercially available malware solutions are sometimes heavily priced. An alternative is VMRay, a malware analyzer that you can use during incident response. VMRay is invisible to malware. Sat File Viewer Free Download. It is embedded in the hypervisor and analyzes malware behavior from that vantage point. As a result, threats execute as they would in the wild. This analysis provides a full function log, which allows you to understand the execution steps of the malware. You can use a web interface to log into the sandbox environment where the malware is executing, possibly simulating the behavior of a normal user. VMRay is not available for free, but nearly everyone can get a 3. Some of these accounts can be extended by exception for researchers without budget, for example for free on an annual basis. Be Careful What You Share. Anything that you share with a public resource is accessible to everyone including the bad guys. Always verify that the sample youre about to upload does not contain confidential or sensitive information. Instead of submitting the file, you can also generate the file hash and verify whether the hash is known by the sandbox. This allows you to access the analysis details, provided the file has been analyzed before, without submitting your actual sample. You may also want to investigate whether the sample is targeted specifically to you. Uploading it to a public sandbox makes the attacker aware of the malware detection.